FileOpen User Experience
No passwords or downloads necessary
Seamless end-user experience
Your end-users are your customers and stakeholders, so FileOpen security is designed to be invisible to the authorized user and impenetrable to anyone else. Since today's workflows are increasingly based in the browser, FileOpen now offers a means to deliver secure content into an unmodified browser. Our BrowserUX solution works in any modern browser on any platform, so your target users can view documents without any download or installation.
FileOpen-protected documents rendered in the browser can enable or disable download, printing, text copy, annotation and other functions, They may be watermarked with user-specific information, and are always under the control of the publisher's server-enabling expiration, revocation, concurrent-usage limitation and other features.
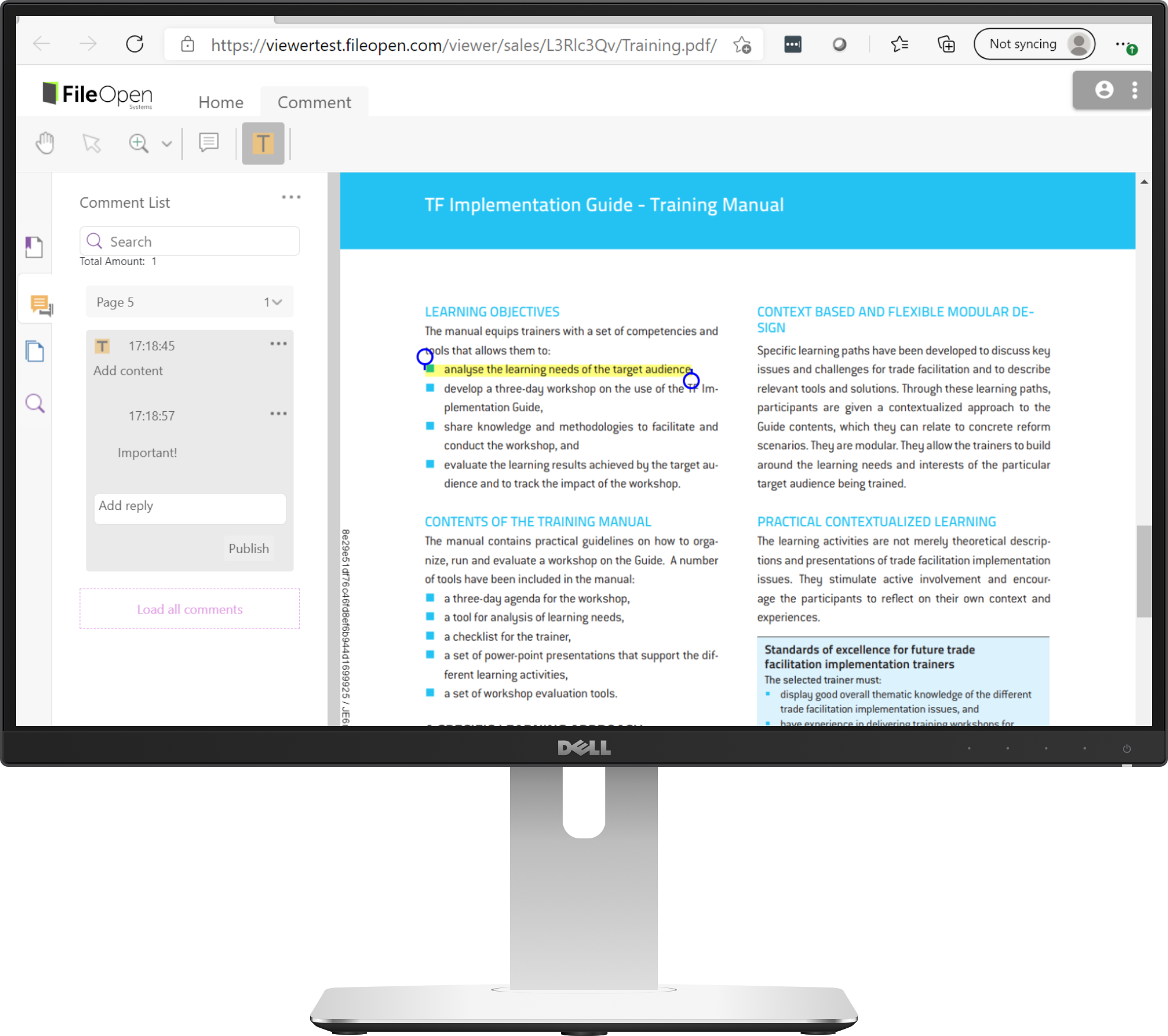
Client Options for Extra-Strength Security
For workflows with desktop applications, FileOpen's original client solutions are still available for Adobe Acrobat/Reader and other PDF viewers as well as MSOffice. When installed onto the local operating system, the FileOpen Client is able to monitor and control the entire user experience for an encrypted document. This control includes dentifying the specific hardware and software being used, the identity of the logged-in user, and complete replacement of application functions around printing, text extraction, annotation and editing with more secure versions that can regulate these activities in accordance with server-side rules.
The same encrypted document can be distributed to the browser and/or to the desktop. So some documents can be delivered to the browser and others only to the desktop, or some users given access to content in the browser and others only on the desktop. And these rules can change at any time.
Enable different permissions for different users
In the FileOpen model, all control is imposed at the time of access, so different users may access the same document with different permissions or the same user granted different permissions at different times. This abstraction enables the imposition of rules to support almost any kind of business logic, for any number of users and documents. The system supports workflows that maximize security and workflows that minimize user friction, or any combination of the two.

